

Access to production assets needs to be controlled, but that incurs major operational overhead. Security and DevOps teams use Entitle to ensure authorized users seamlessly gain just enough access, just in time.
Accelerate access via self-service requests, decentralized approvals, and automated provisioning, while maintaining security guardrails such as duration limits and tiered approvals.


Remove barriers standing between your team and the permissions they need during emergencies via automated approvals and JIT provisioning for users in an on-call schedule.

Ensure every access to customer data is specific and time-bound. Create approval workflows based on groups, roles, support tickets, and so on.
New: Your customers can now authorize user access to their data, showcasing an enhanced commitment to their privacy.


Rather than depending on the risky practice of using shared secrets, users requiring access to databases and non-federated systems are provided with a new, temporary account endowed only with needed permissions. This account information is securely delivered to the user, and the entire process is fully auditable.
Designed for simplicity and flexibility, you can easily view users, identities, integrations, resources, and roles. Administrators gain powerful visibility, overseeing all permissions, including ones that were not granted through Entitle. More about cloud access governance

Set up in minutes, rollout in days. No professional services needed.

Users can request access and approvers are notified seamlessly through Slack, MS Teams, Jira, or various other interfaces. Each request contains necessary approval information such as required permission, duration, and justification.


Use Entitle’s APIs and Terraform Provider to manage access controls using Infrastructure-as-Code (Iac). Customize our solution to fit your environment.

Assign managers, resource owners, or groups as dedicated approvers for access requests. Once approved, provisioning occurs automatically inside the app. Access is then automatically de-provisioned when access expires.

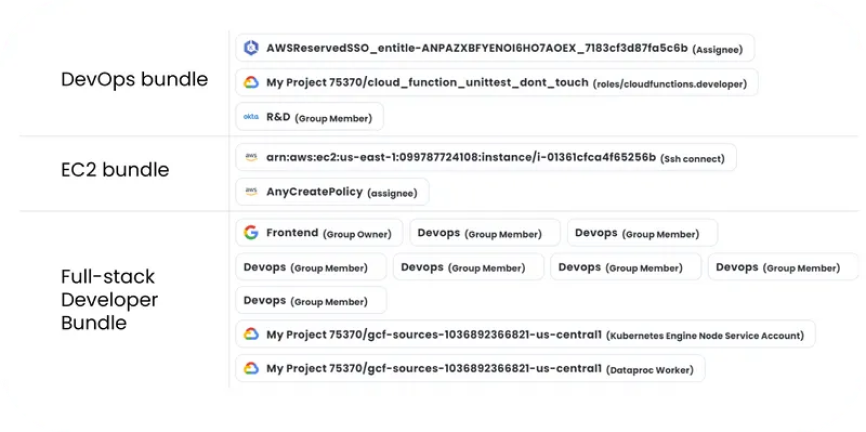
In one request, employees can get just in time access to assets from different applications like AWS S3 buckets, MongoDB collections, SharePoint folders, and Slack channels.
Use a centralized view to understand who was granted access to what resources, who authorized it, the justification, the duration, and the exact timing. Track user activity within the third-party applications, ensuring compliance and integrate with your SIEM.

Explore JIT access integrations
Install in minutes, Roll out in days